Understanding AWS Identity and Access Management (IAM)
Subtle Guardians: Fortifying AWS Security with IAM
In the rapidly evolving landscape of cloud computing, security is paramount. As organizations migrate their infrastructure and applications to the cloud, managing access to resources becomes a critical concern. AWS Identity and Access Management (IAM) is a powerful service provided by Amazon Web Services (AWS) that addresses this need by securely controlling access to AWS services and resources.
What is AWS IAM?
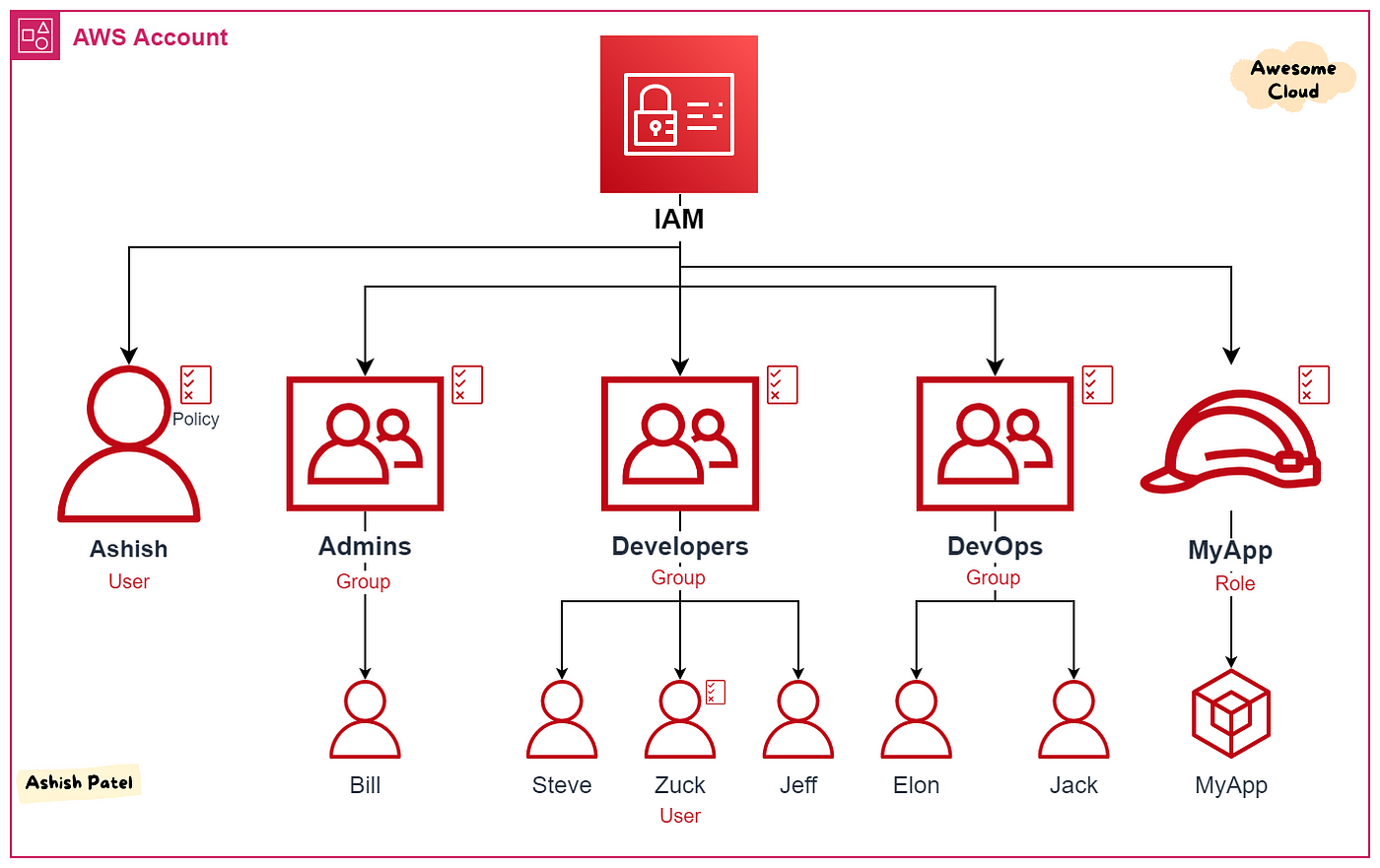
AWS IAM is a web service that enables you to securely control access to AWS services and resources. It allows you to create and manage users, groups, and roles, and assign permissions to them to access or manage AWS resources.
Key Concepts in IAM:
Users: IAM users are individuals within your organization who interact with AWS resources. Each user has a unique set of security credentials (such as a username and password or access keys) that are used to access AWS services programmatically or through the AWS Management Console.
Groups: IAM groups are collections of IAM users. By organizing users into groups, you can manage permissions more efficiently. Instead of assigning permissions to individual users, you can assign them to groups, and all users in the group inherit those permissions.
Roles: IAM roles are entities that define a set of permissions for making AWS service requests. Unlike users and groups, roles are not associated with a specific IAM user or group. Instead, they are assumed by trusted entities such as IAM users, AWS services, or external identity providers.
IAM Policies:
IAM policies are JSON documents that define permissions. They specify what actions are allowed or denied on what AWS resources. IAM policies consist of policy statements that describe the permissions and the resources to which they apply.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:*",
"Resource": "*"
}
]
}
IAM Best Practices:
Principle of Least Privilege: Grant only the permissions required to perform a task. Avoid granting unnecessary permissions to users, groups, or roles.
Regularly Review Permissions: Regularly review IAM permissions and policies to ensure they are up-to-date and aligned with organizational security policies.
Enable Multi-Factor Authentication (MFA): Require IAM users to use MFA to add an extra layer of security to their accounts.
Create IAM Roles for Applications: When running applications on Amazon EC2 instances, use IAM roles to grant permissions to the applications rather than embedding access keys directly into the code.
IAM Security Features:
IAM Access Analyzer: IAM Access Analyzer helps you identify resources that can be accessed from outside your AWS account. It analyzes resource policies and generates findings to help you identify and remediate unintended access.
IAM Policy Simulator: IAM Policy Simulator allows you to test the effects of IAM policies before applying them. You can simulate different access scenarios to understand how IAM policies impact access to AWS resources.
IAM Credential Reports: IAM Credential Reports provide you with details about IAM users and their access keys. You can use these reports to monitor access keys, detect unused keys, and identify potential security risks.
Conclusion:
AWS IAM is a fundamental component of security in the AWS cloud. By understanding IAM concepts and best practices, organizations can effectively manage access to AWS resources and protect their data and applications from unauthorized access. By following IAM best practices and leveraging IAM security features, organizations can strengthen their security posture and ensure compliance with industry regulations.
